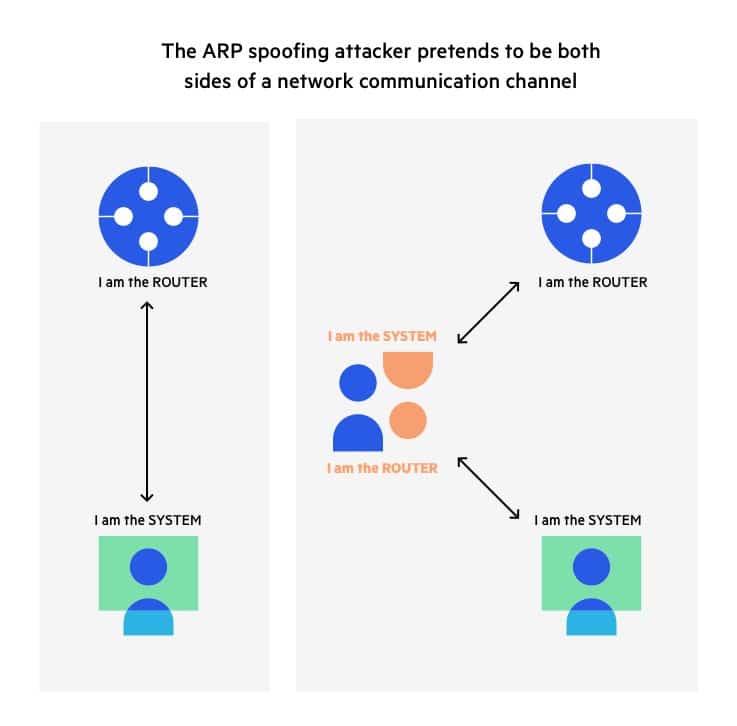
Exemplary Info About How To Prevent Arp Attack
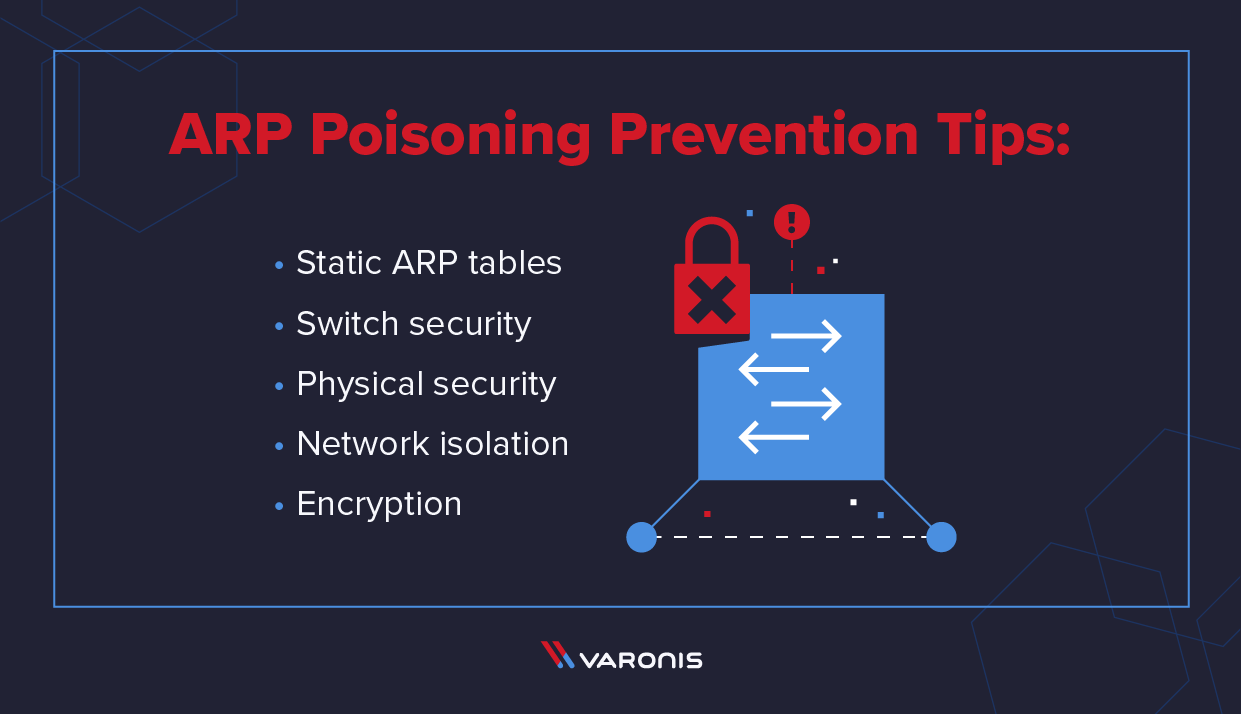
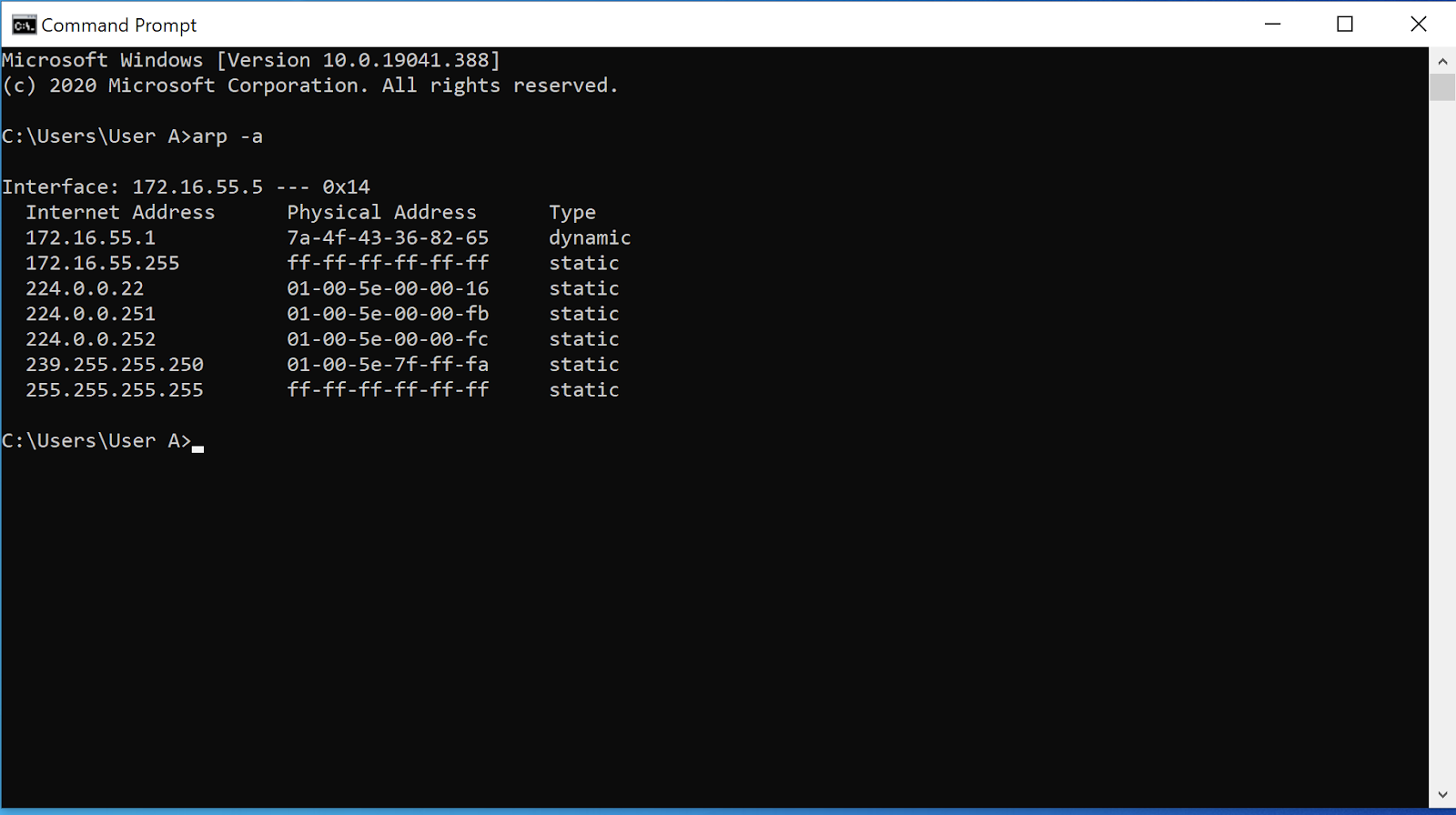
How to prevent arp poisoning attacks static arp tables.
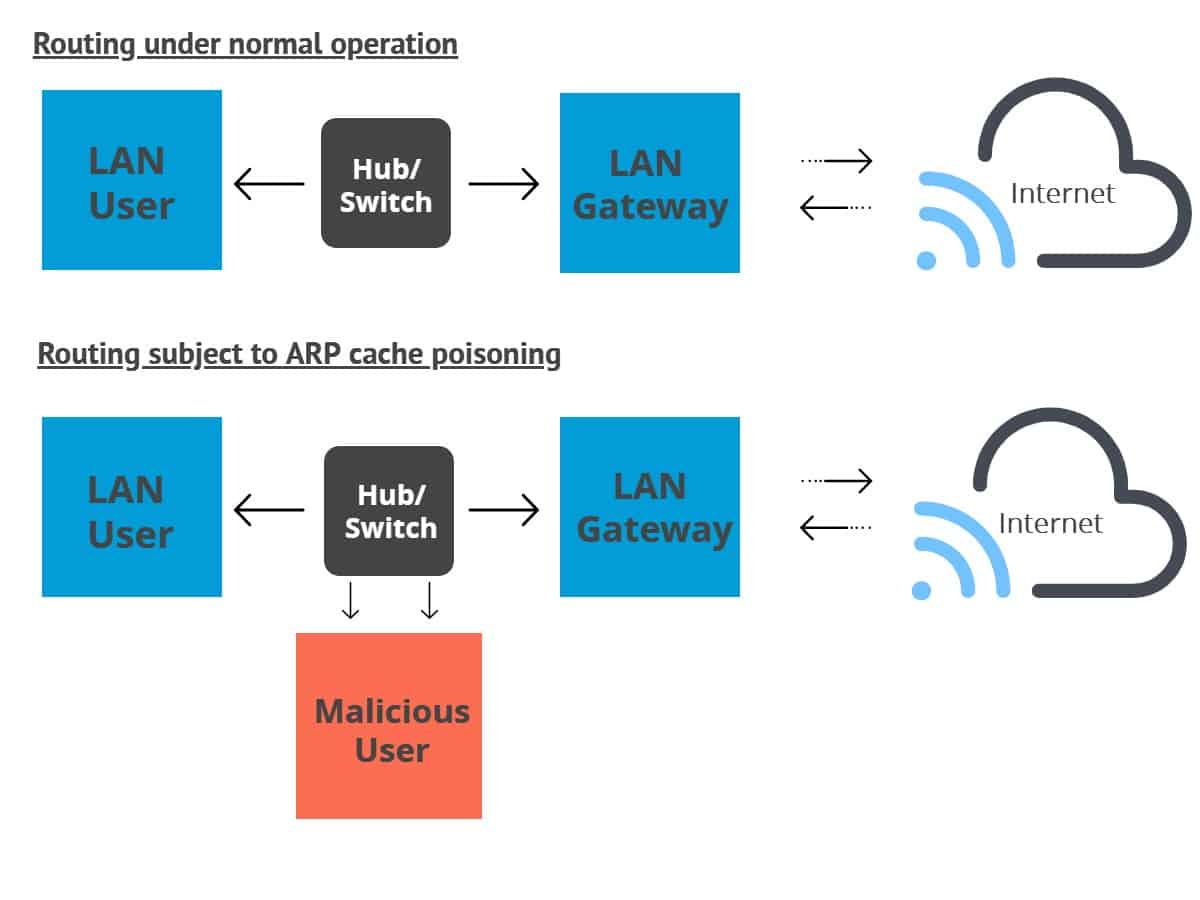
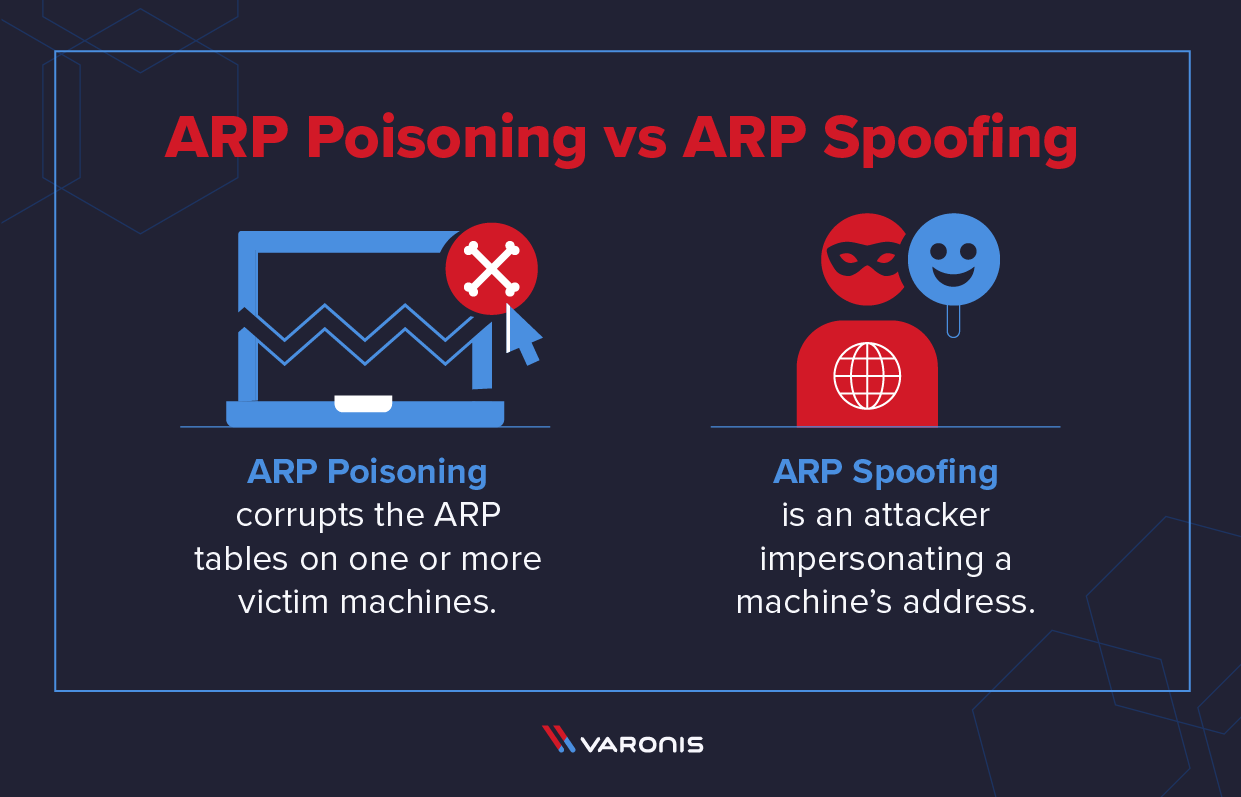
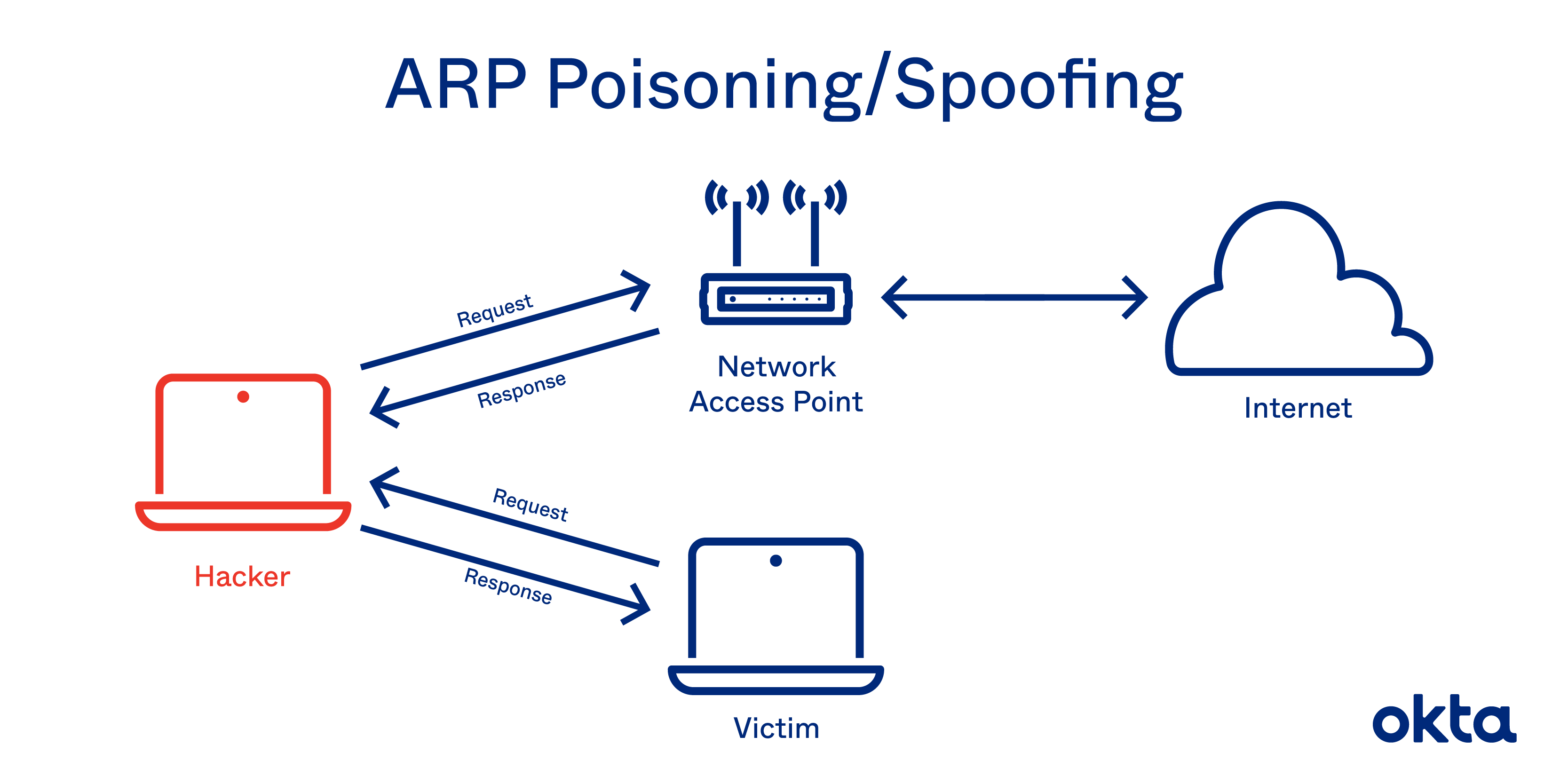
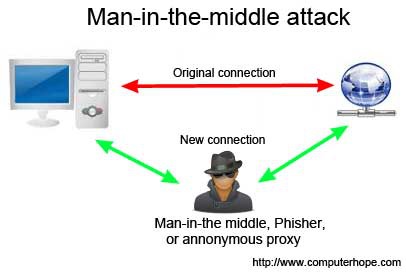
How to prevent arp attack. Authenticating a data sender’s identity in some way can prevent receiving data from a. So, it will prevent devices from listening on arp responses for that address. In the past few months, we’ve seen the term “arp.
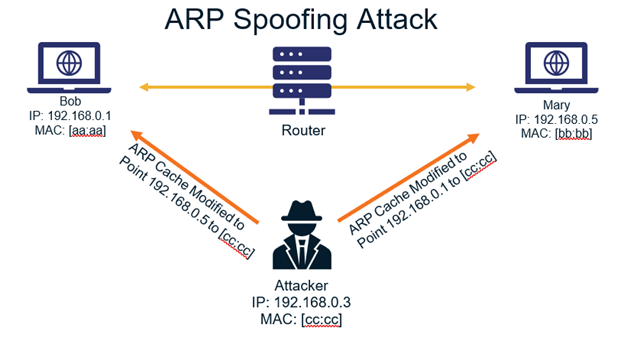
Use static arp to allow static entries for. They send a spoofed arp packet, they send a request that connects to the spoof, and they. Hackers and unethical attacks on networks provide a continuing threat to take information and cause digital mayhem.
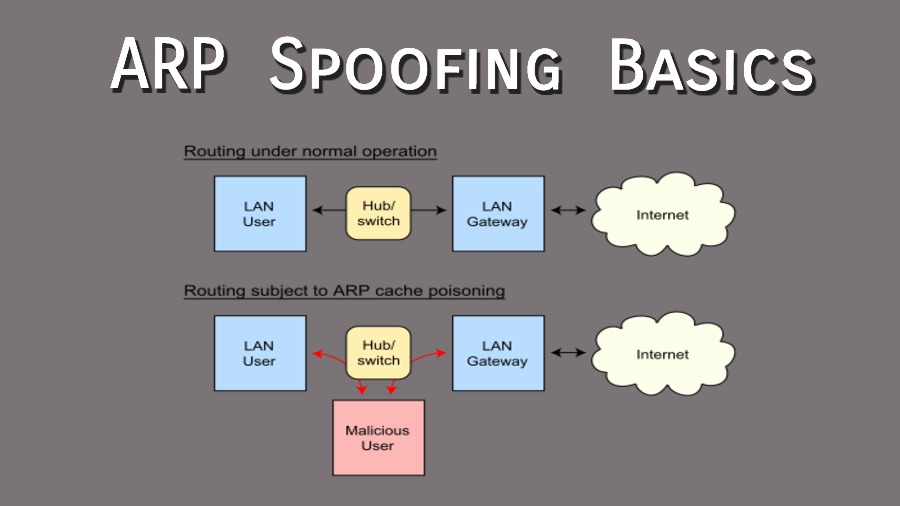
How to prevent arp attacks tags: From the way of affecting network connection, there are two possible arp attacks, one is cheating computers and other is one cheating router. How to set on the router to prevent arp cheat?
Firstly, make sure that all devices on your network have unique mac. In the meantime, there are a few things you can do to protect yourself from arp spoofing attacks. Use the arp attack protection page to specify how to protect your network against common types of arp attacks and configure the ip&mac binding rules.
Type the username and password in the login page, the default username and password both are admin. This video showing how to stop arp attacksoftware contact :9176719244 Of course, the two attacks may occur at.
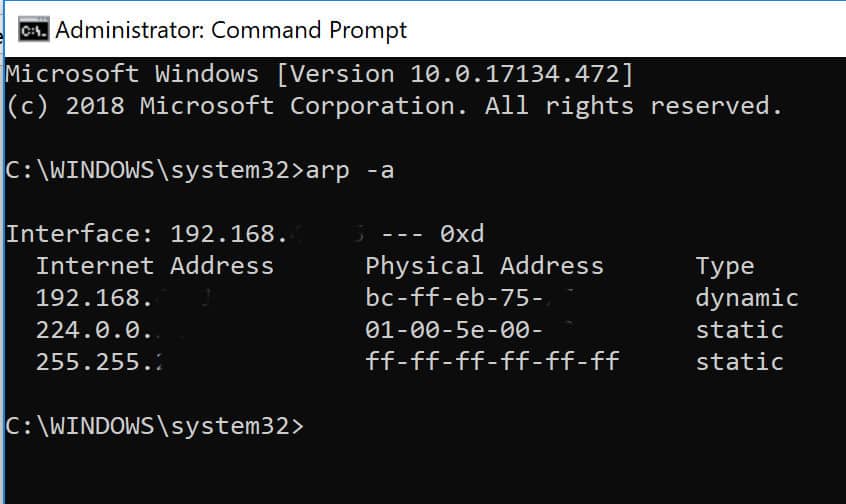
Every bit of sensitive data that you send to your server including your login password, is visible to the attacker. Let’s discuss the four most effective and commonly used ones. The arp protocol allows you to create a static arp entry for an ip address.